Welcome to Part 2 of our mini blog series on how to set up different secure communication methods for Cassia’s Bluetooth Gateways and IoT Access Controller (AC). The second blog in our mini-series will focus on secured MQTT for gateway to AC communication.
Currently, all Cassia gateways support and only use secured MQTT which runs on port 8883. At Cassia, we take the security of our customer’s data very seriously, and for that reason, no gateways use unsecured MQTT. In addition, Cassia’s gateways use TLS 1.2 protocol for enhanced security.
Secured MQTT between the gateway and AC is designed to enable secured communication. The TLS protocol is also designed for secured communication, and the MQTT protocol is designed to allow lightweight, low-overhead communication.
End-users can rest assured that the data being transferred between gateway and AC is secured at all times. Because MQTT relies on TCP, communication will be far more stable when sending data because of an ordered, lossless and bi-directional connection.
The settings for Secured MQTT can be found on both the AC and local gateway webpage. By default, both the AC and gateway use TLS certificates provided by Cassia Networks. Custom TLS certificates can be configured. End-users will need to obtain or generate the CA certificate, server certificate, server private key, client certificate, and client private key.
The steps and screenshots below outline how to properly setup and configure for both the local gateway webpage and AC.
Instructions for the Access Controller:
- Log in to the AC.
2. Go to the Settings page.
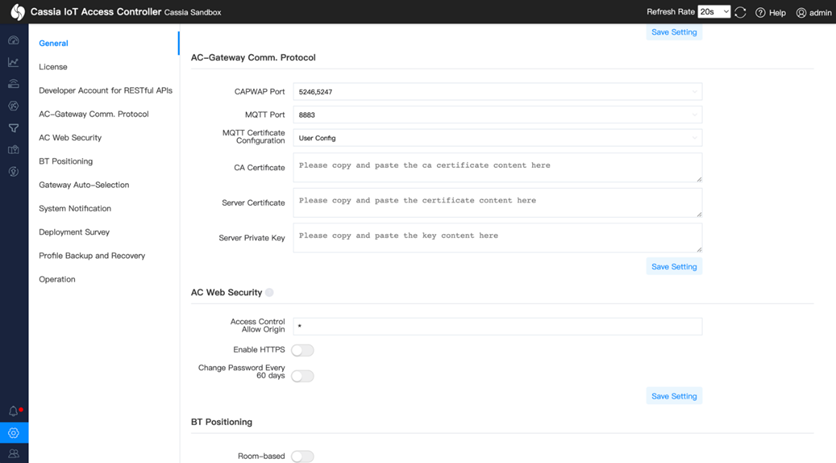
3. Scroll down to “AC-Gateway Comm. Protocol”.
4. Under “MQTT Certificate Configuration”, select “User Config”.
5. Fill in the details for CA Certificate, Server Certificate, and Server Private Key.
6. Click on the “Save Setting” button.
Instructions for the Local Gateway Webpage
- Log in to the local gateway webpage.

2. Go to the Other tab.
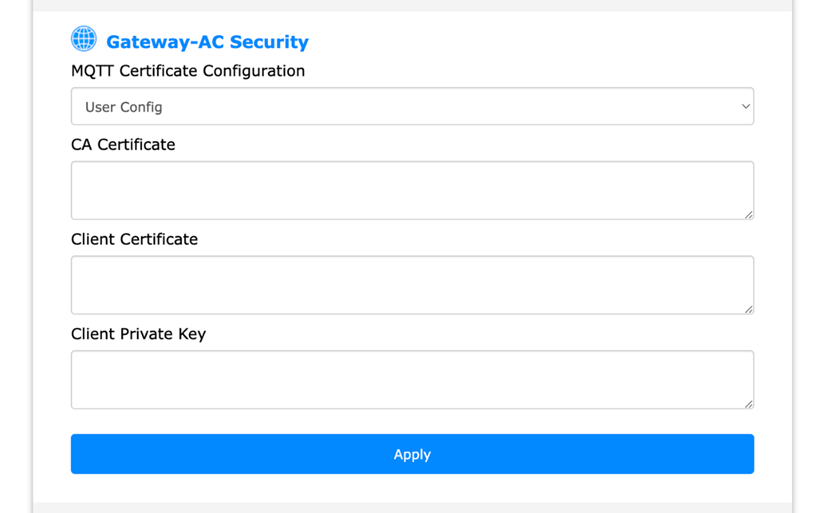
3. Scroll down to the “Gateway-AC Security” section.
4. Under “MQTT Certificate Configuration”, select “User Config”.
5. Fill in the details for CA Certificate, Client Certificate, and Client Private Key.
6. Click on the Apply button.
The steps outlined above will allow end-users to properly set up and configure secured MQTT for both the local gateway webpage and AC.
Stay tuned for part 3 of our mini-series where we will focus on secured communication between the gateway and MQTT broker for the gateway’s MQTT Bypass feature.
Interested in learning more or need help finding this feature? Contact our support team at support@cassianetworks.com.








