Welcome to the last part of our mini blog series on how to set up different secure communication methods for Cassia’s Bluetooth Gateways and IoT Access Controller (AC). The third blog in our mini-series will focus on MQTT data bypass.
Currently, all Cassia gateways support MQTT bypass. This feature is designed to direct all MQTT data to an external server while keeping the control path with the Cassia AC.
In simpler terms, this means that all the data collected from devices will be directed to the user’s MQTT broker server while the gateway’s operations are still controlled by the AC.
The end-user will have the ability to direct their sensor data to their servers without having to go through the AC. This reduces the time it takes for data to be collected. Separating the gateway’s operations from the sensor data allows the user the ability to continue using the power of the AC while having data sent directly to the MQTT broker server.
The MQTT bypass feature also allows TLS Certificates and Pre-Shared Keys (PSK) for secured communication.
The steps and screenshots below outline how to properly set up and configure this feature.
Instructions for the AC:
- Log in to the AC console
- Go to the gateways page
- Click on a gateway row and click on the Config tab.
- Scroll down and expand the Bypass section.
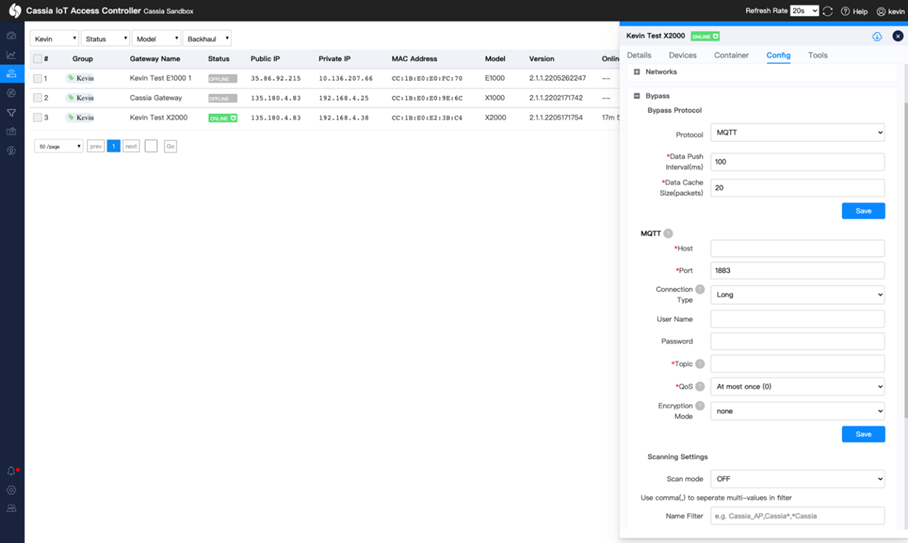
It’s important to note that when using the gateway in Standalone Gateway mode, the features of MQTT Bypass are still available (without the AC managing the gateway’s operations). To access the MQTT Bypass features of the gateway, follow the steps below:
- Log in to the local gateway webpage.
- For “Gateway Mode”, select “Standalone Gateway”.
- Scroll down and click Apply. Wait for the gateway to reboot.
- Log in again after the gateway reboots.
- Go to the Service tab.
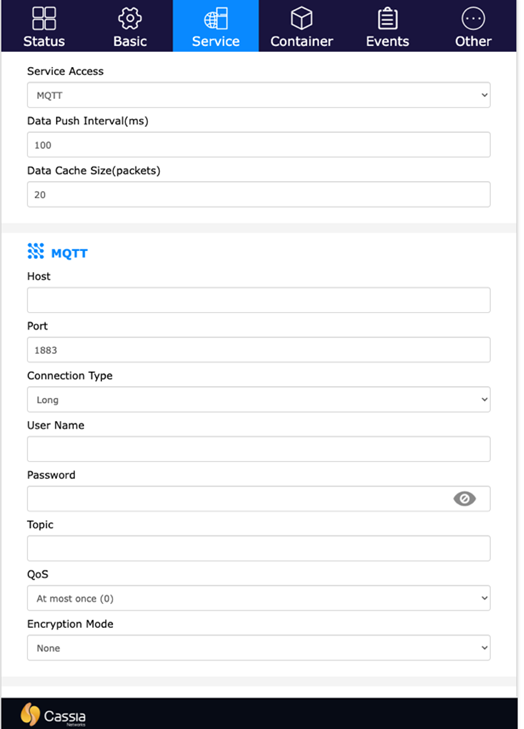
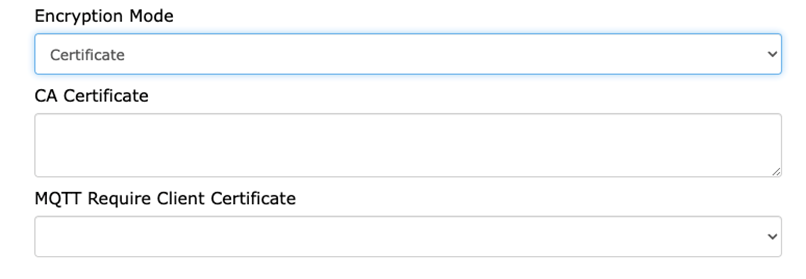
Both the AC webpage and the local gateway webpage allow the end-user to set up TLS Certificates and Pre-Shared Keys (PSK) for MQTT Bypass communication. Both can be found under the “Encryption Mode” option.
For PSK, please ensure you have the PSK key and the PSK identity ready.

For the Certificate, make sure to have the CA certificate ready. The “MQTT Require Client Certificate” option allows end-users to require MQTT to use a client certificate as well.
The steps outlined above will allow end-users to properly set up and configure MQTT data bypass for AC.
For more information on the MQTT Bypass feature, please see Chapter 5.6 “Service Tab” found in the Cassia User Manual.
Interested in learning more or need help finding this feature? Contact our support team at support@cassianetworks.com.