What is a TPM and what does it do?
TPM was originally created by a consortium called the Trusted Computing Group (TCG) in 2003 to enable trusted computing features in computers, mobile devices as well as network equipment.
A TPM, or Trusted Platform Module, is a computer chip that can securely store artifacts used to authenticate a platform such as a PC or laptop. Example of artifacts include passwords, certificates and/or encryption keys. TPM secures these artifacts with a secure algorithm integrated into your computer’s hardware. TPM chips also provide safe storage of these artifacts used for logging into online services and provide a higher level of security than software alone to protect sensitive data against malware and hackers. This is especially important for industrial computers, which store massive amounts of data about an organization, and medical computers, which store highly sensitive patient data.
How does TPM work?
Most of the data we transmit throughout the day is sent unencrypted, usually as plain text. TPM chips essentially use a mix of software and hardware to protect any important passwords or encryption keys when they are sent in this unencrypted form. If a TPM chip senses that a system’s integrity has been compromised by a virus or malware, it can start up in a quarantine mode to help resolve the issue.
How many different types of TPM exist?
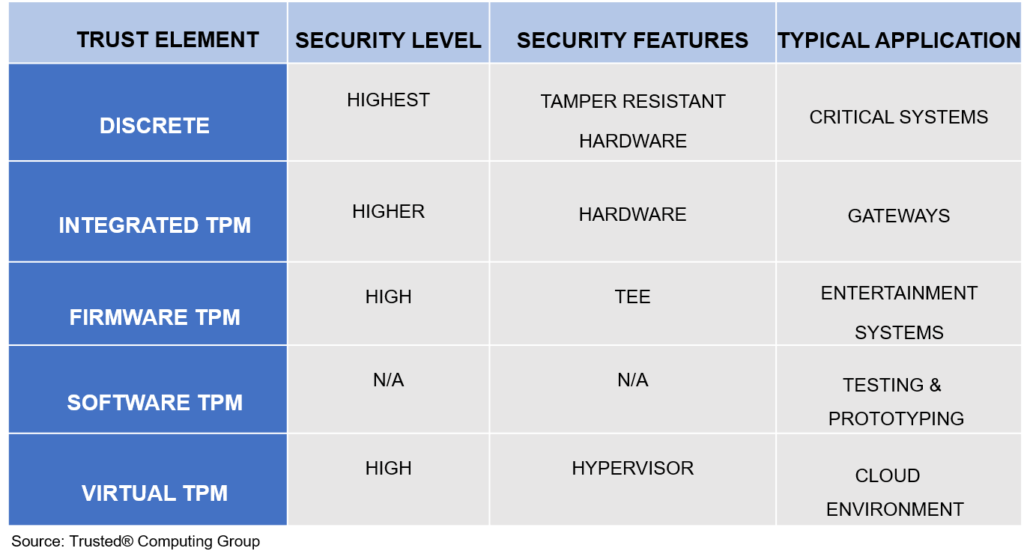
Currently, there are five different types of TPM. See figure 1 below for a comparison of these types as well as their applications.
Where is TPM used?
TPM has become the standard in the majority of consumer grade computers since its inception, but it is now being used in high-risk industrial devices and in many industries including the IIoT, automotive, e-commerce, government and healthcare. Furthermore, enterprises that use mission critical applications, such as email and document management, that require strict security measures can benefit from stronger protection when using a TPM.
Did you know?
Cassia’s latest X2000 Enterprise Bluetooth Gateway has a TPM chip that supports secure boot, trust boot, secure storage, and other crypto-chip based security functions. Cassia is strengthening its Bluetooth gateways with advanced security solutions to help customers secure their networks and provide optimized protection against malicious attacks.
Ready to learn more about Cassia’s Bluetooth Gateways? Email our sales team at sales@cassianetworks.com for a free demo.